5 Security Stages of the DevSecOps Pipeline

DevSecOps builds on modern DevOps practices by incorporating security processes and automation into the development pipeline. This enables development teams to continue the rapid and continuous delivery trend while improving software assets' security. The DevSecOps pipeline follows the familiar DevOps “infinity loop” structure while incorporating some extra steps to ensure code security before, during, and after it’s pushed to production.
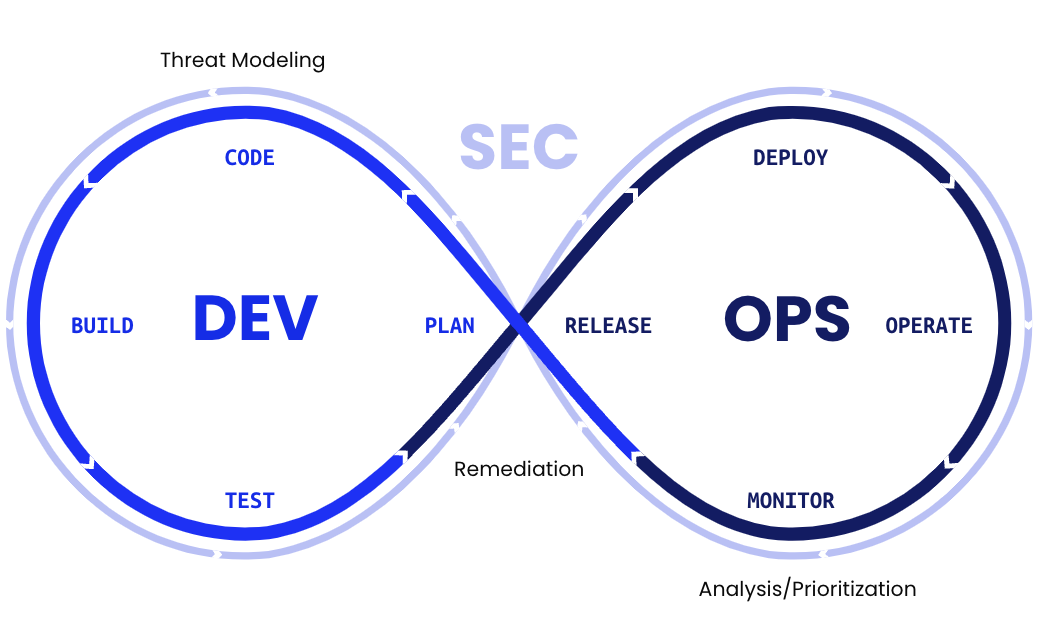
5 Security Stages In-Depth
A typical DevOps pipeline contains eight stages. The DevSecOps pipeline retains all of these and adds five more that are specific to security:
1. Threat Modeling
Threat modeling in DevSecOps attempts to determine the risks associated with a software asset and the most likely ways an attacker might try to compromise it. This process, which is typically supported by security teams, includes a range of activities:
- Analyzing the environment the application operates within
- Determining possible attack targets (e.g., sensitive customer data)
- Outlining possible attack scenarios (e.g., OWASP Top 10 threats or abuses of legitimate logic)
- Predicting the most likely sources of vulnerabilities
These steps help an organization determine how much risk a new or updated software asset could generate—and, most crucially, help development teams proactively identify mitigation options for the most likely security issues and risks.
Consistently including threat modeling in the DevSecOps pipeline also helps development teams understand how security and development intersect and can help reduce risk for the organization.
2. Security Testing
Security testing is the first operational stage in the DevSecOps pipeline. Automated security scanners play a crucial role here and are often the first (and simplest) security control integrated development workflows. Static, Dynamic, and Interactive Application Security Testing (SAST/DAST/IAST) scanners are an excellent way to uncover simple vulnerabilities in code before it’s pushed to production.
However, scanners are not the only security testing practice included in a DevSecOps pipeline. Others include:
- Manual and automated code reviews—these processes are essential to uncover bugs, inefficiencies, and other issues in newly-written code that automated security scanners can’t find.
- Security assessments and pentests—while not fast enough to incorporate into every cycle, security testing by skilled hackers is the first opportunity to expose a software asset to real-world threats.
3. Analysis and Prioritization
Typically, the security testing stage of a DevSecOps pipeline uncovers plenty of potential issues and vulnerabilities, particularly for new or significantly modified software assets. However, most organizations don’t want to wait for developers to resolve all those issues before pushing code to production—that would slow the pipeline down too much and potentially disrupt business objectives.
Instead, the DevSecOps pipeline includes the analysis and prioritization phase to help development teams identify and resolve the most significant risks. Development teams review all of the potential threats and vulnerabilities uncovered during the security testing stage, aggregate them into a master list, and prioritize them based on their potential business impact and the likelihood of exploitation—in other words, by the risk they pose to the organization.
The security team typically supports this stage, as it requires a strong understanding of the organization’s threat landscape, compliance obligations, and the consequences of a successful attack.
4. Remediation
After prioritizing all outstanding vulnerabilities and issues, the next step is for the development team to remediate them. The security team may continue to support this process by educating developers on the nature of different threats and possible remediation options. Alternatively, a development team may take complete ownership of this process over time.
Typically, developers can push the code to production after remediation of specific vulnerabilities —or after the reduction of overall risk associated with an asset is at an acceptable level. Development teams can then address identified vulnerabilities in future code releases so that overall risk continues to decline over time.
5. Monitoring
Monitoring is a post-push stage of the DevSecOps pipeline where development teams track the overall security posture of a software asset as it runs in production. This stage is essential to uncover new vulnerabilities or misconfigurations that can occur over time or even spot weaknesses that were always present but missed by pre-push security practices.
The monitoring stage can include various security practices, such as:
- Regular completion of security assessments and pentests to see how a production software asset holds up against real-world threats.
- Using bug bounty and Vulnerability Disclosure Programs (VDPs) to provide a continuous source of vulnerabilities, misconfigurations, business logic abuses, and other issues that a malicious actor could exploit.
Even with “perfect” DevSecOps processes, it’s impossible to uncover all issues and risks associated with a software asset before it reaches production. Rapid change means the likely introduction of new issues over time or new and unpredictable threats. The monitoring stage helps development teams track and reduce a software assets risk profile over time, ensuring it remains resilient to attacks while fulfilling its business purpose.
DevSecOps is an Ethos, Not a Prescription
It’s important to understand that while the DevSecOps pipeline diagram above appears straightforward, each organization’s implementation of DevSecOps is different. Not all security practices can be incorporated before every code push—particularly for development teams with rapid cycles. For example, a team that pushes code twice daily can’t expect to complete a manual code review before every push.
Instead, each organization should experiment before settling on a DevSecOps pipeline that balances the need for security against operational concerns such as speed, resources, and risk management.
Improve DevSecOps with HackerOne
HackerOne provides access to the world’s largest community of ethical hackers, who possess a complete range of testing skills and expertise to help development teams find and resolve vulnerabilities in software assets. These include:
- Threat modeling support via HackerOne Insights
- Automated and manual code reviews-as-a-service
- Security assessments and pentests completed by hackers with domain-specific expertise
- Continuous testing via bug bounty or VDP
- Successfully resolved validation that issues via HackerOne Retest
We design our services to support the modern DevSecOps pipeline. HackerOne’s Attack Resistance Management Platform helps development teams secure their pipelines and close the attack resistance gap, so many organizations face today—the difference between assets you know and can defend and the unknown and unprotected—by continuously improving visibility and remediation across your evolving attack surface. We help you achieve attack resistance. Contact us to learn more.
The 7th Annual Hacker-Powered Security Report
